Multi-factor authentication (MFA) is a protective tool to add an extra layer of security when logging into various accounts and services over the internet. It simply means that in addition to the usual account password, the account owner should know or have another thing to be able to log in.
Its subset, two factor authentication (2FA) means that it needs one extra piece of evidence to be able to access digital services. These verification factors should always come from different categories, so while two passwords would technically be enough for 2FA, they wouldn’t add much security.
When logging in to an MFA enabled service, you’ll be asked to provide another category of evidence (called factor) to further prove your identity, like a different kind of second password.
Authentication factors
Factors are the different things that can be used to log in in addition to the usual password. They come in various shapes and forms, such as
- SMS authentication
- E-mail verification
- Software token
- Hardware token
SMS authentication
Adding SMS as a protective measure to an account login is the simplest way to increase the security of authentication. After successfully entering your password to log in, the system sends a text message to your previously set phone number and it’s only possible to complete authentication after entering the code from the SMS. These messages are typically valid for a few minutes only and they can only be used once.
The drawback of this system is that SMS travels in clear text so it’s technically possible to listen to / copy it with specialized equipment. It is also vulnerable to hijacking a cell phone number by simply cloning a SIM card. In recent years there have been multiple high-profile incidents involving logging into crypto exchanges and draining vulnerable accounts dry by cloning the owner’s SIM card using simple social engineering (calling the provider and impersonating the original owner, asking for a new SIM card).
E-mail verification
This one works by sending you an e-mail every time there is a login attempt from a new computer. It either includes a code to be entered as a second factor or there is a clickable link to complete authentication.
While the security this provides is low, it still way better than having no 2FA at all. However, if someone has access to your e-mail, they can possibly use it to a) reset your password to the service, b) use the same e-mail address for 2FA confirmation. It should be avoided, when possible.
Software token
These tokens work by running specialized software on a secondary device (typically a mobile phone). These can handle multiple 2FA accounts/services – first, they should be connected to the service (see below), this should only be done once for each account. Once set up, the software displays a 6-8 digit number that serves as an extra password when logging in. This number changes every 30-60 seconds and can be used once.
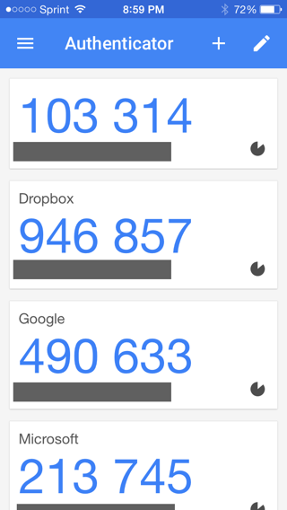
The advantage of this is system is that it’s very easy to use and it needs no internet access on the device to function. The only requirement is that the device’s clock should be set up correctly because the code is derived from the current time.
There are various free and paid software solutions that implement 2FA functionality, for example
- Google Authenticator
- Microsoft Authenticator
- Authy
They all work the same way and are mostly interchangeable. Authy is my favorite solution, it works on both Android and IOS and it also provides cloud backups (encrypted) and the possibility to sync 2FA accounts across multiple devices.
Hardware token
The most secure of them all, they are dedicated hardware gadgets, similar in size to USB flash drives. Some of them are tied to a service and they have a display like this:

Others are pluggable into the computer (some even work over Bluetooth and compatible with phones). They often provide various extra security features – most importantly the code generation happens inside the gadget and they cannot be stolen by malware – they can easily be lost though.

Their drawback is that it’s not something you can simply download and start using and only a small subset of security-conscious users are willing to take the extra step to acquire one.
Back-up methods for 2FA
The security of having multi-factor authentication comes at the cost of convenience – the whole point of this exercise is to stop anyone without your second factor from logging in.
It unfortunately also means that losing your authentication token or access to your mobile phone number will effectively make it impossible to log in. On the other hand, making it too easy to recover access would also help the very people you’re trying to protect your account from.
With all this in mind, there are various options to recover a 2FA enabled account – not all of them are possible with all vendors and they also effectively decrease the security provided by multi-factor authentication.
Recovery codes
When enabling software or hardware tokens, you’re often presented with a list of one-time use special codes that can be used to either disable or temporarily skip 2FA logins for one session. These should be saved separately (NOT stored together with your password), possibly printed and kept in a safe place. Together with the account password, they provide valuable back-up access to protected accounts.
Back-up phone numbers / SMS backup
It’s also possible to add a second phone number and/or extra SMS number to send back-up 2FA codes, should the primary authentication method be unavailable / lost. This obviously has security risks because it effectively renders the primary method useless, anyone can hijack the secondary phone and use that to log in. Unfortunately, most providers won’t even allow disabling it altogether, meaning that it doesn’t matter how secure authentication tokens are, there will always be a weaker method, similar to having a blast-proof concrete entrance door and a half-open window in the backyard.
Software token backups
Losing your phone with the 2FA software on it is one of the worst possible ways to lose access to all the 2FA protected accounts at once so it’s a good idea to prepare for such incidents in advance. SIM cards can eventually be replaced to gain access to your mobile phone number again, however, it’s also possible to back up software token codes or transfer them in advance.
Google Authenticator provides a recent feature to transfer 2FA accounts to another phone/account but it works between Android phones only. Authy has cloud backup, you can simply upload your encrypted codes to your cloud account and simply run Authy on another mobile phone or computer. Remember, running a 2FA client on the same computer is insecure and should only be used as an emergency measure.


