The root password is the final security barrier that protects a Linux system’s administrative account from unauthorized access. If the password is lost, it becomes impossible to administer the system and make configuration changes, so let’s look at different ways to recover it.
Needless to say, techniques here are only to be used on your own system – unauthorized system access is a crime in most jurisdictions.
Where and how are Linux passwords stored?
Technically, all local account passwords are saved in the /etc/shadow file in a hashed format. It’s a tech file, where fields are separated by colons and it is readable by any text editor. Hashing means that the ability to read the file doesn’t grant access to the system because of the nature of password hashes.
# head /etc/shadow
root:$6$2T1VTUx5$Y.DoVs.TDUxSQhTfU3JG2b4MZENVuPYdTxg408trBaZNjiIoplqFaWyx/josr9u0BEhYFTdjoxzJc//SrJGVk1:18772:0:99999:7:::
daemon:*:17793:0:99999:7:::
bin:*:17793:0:99999:7:::Here, the root password is set to “techtipbits” and that long gibberish after “root” is the password hash. The hash itself has three parts, separated by the $ sign.
The first part (6) tells the format of the hash, the second one (2T1VTUx5) is the salt, the third one (Y.DoVs.TD…) is the hashed password. The salt is random data that’s used to make dictionary attacks (pre-computed hashes) difficult because each password is “salted” with a random hash in addition to the password.
By default, the password is hashed 5000 times (defined in /etc/logins.def) to slow down decryption attempts.
Introducing John the Ripper
John the Ripper is a tool to decrypt password hashes by quickly trying all possible passwords. Depending on the simplicity of the password and the hash algorithm, it can decrypt simple passwords in hours to days but complicated ones may take forever. It’s downloadable from https://www.openwall.com/john/ and also available as a package in Debian or Ubuntu called “John”.
To show you how it works, let’s change the password to something simple (123456) and crack it:
# passwd
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
# head -1 /etc/shadow > shadow
root@test:~# john shadow
Created directory: /root/.john
Loaded 1 password hash (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
123456 (root)It only took a few seconds because of the simplicity of the password. John also supports hashing using video cards (incidentally, the SHA algorithm used here is similar to the one bitcoin is based on, so a bitcoin ASIC could theoretically be used for password cracking and they can do around 20TH/sec (40.000x as fast as an average CPU).
On a single CPU core (depending on the CPU) John can crack around 500.000 crypt3 hashes, so with the default 5000 rounds per password, it means 100 passwords / second. Using a GPU can speed up things considerably (1000 times on an Nvidia 1080) though.
It’s easy to see that cracking already existing passwords is not really a feasible unless the password itself is short and simple or there are unlimited resources so let’s look at other ways to recover root access.
Rewrite passwords using Sudo
Sudo is a tool to execute commands on behalf of another user, most importantly on behalf of the superuser (root), if allowed. It also allows running a limited subset of commands as another user (root) but it can easily lead to security issues if those commands themselves can be forced to run arbitrary commands or access files as root.
If you have sudo access, it’s pretty straightforward to change the root password. It’s a good practice to use sudo instead of the root in most cases anyways, so it’s possibly to identify who ran commands and also easier to revoke access instead of having to change and distribute the new one.
$ sudo passwd
[sudo] password for techtipbits:
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully“sudo passwd” will first ask for your own password to become root then ask for the new root password twice. This can only be done by users who already have sudo access.
Access the system using Grub
Anyone with local access to the system can force the boot manager to run the system with a custom init script. The Linux boot process ends in starting init, so changing it to a shell will result in instant root access after the boot process is complete. This can be done by passing the “init=/bin/sh” boot parameter to the kernel. Conveniently, Grub allows the editing of boot parameters so with a few keystrokes it’s possible to boot the system by appending this to the active kernel at boot.
Press the key “e” at boot when the Grub prompt shows up, so it launches the boot editor. Find the line that starts with “linux” and append “init=/bin/sh” without quotes. Then pressing F10 boots the system into a root shell.
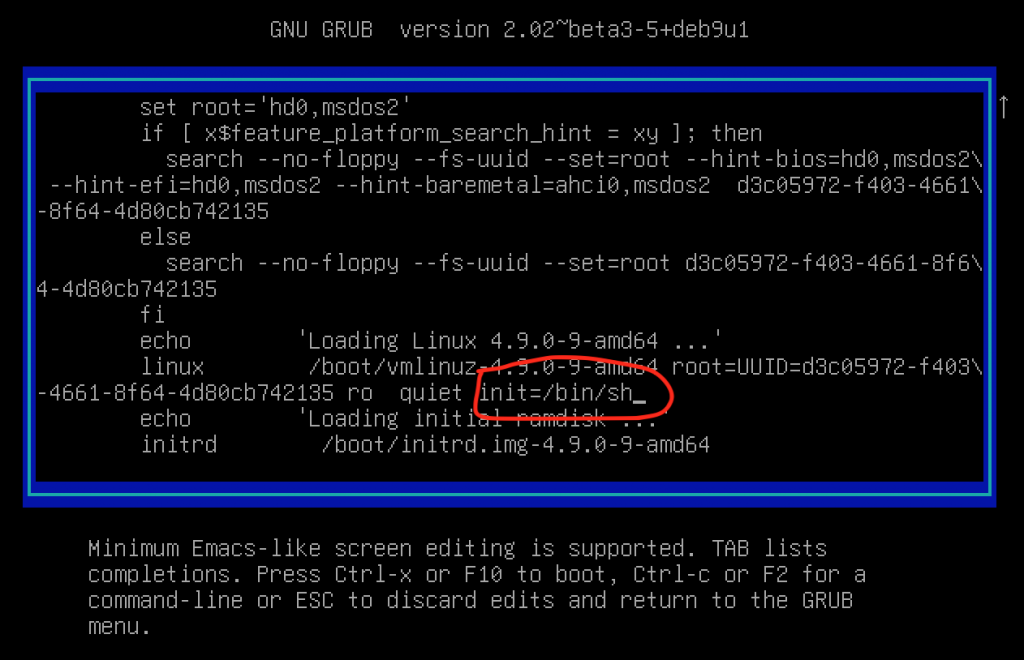
When the root shell is started, you will get basic system functionality but there is one issue, the root filesystem is mounted as read only so it’s not possible to change the password just yet.
You need to remount the root filesystem read-write by running “mount / -o remount,rw” then you can change the password and finally reboot the system.
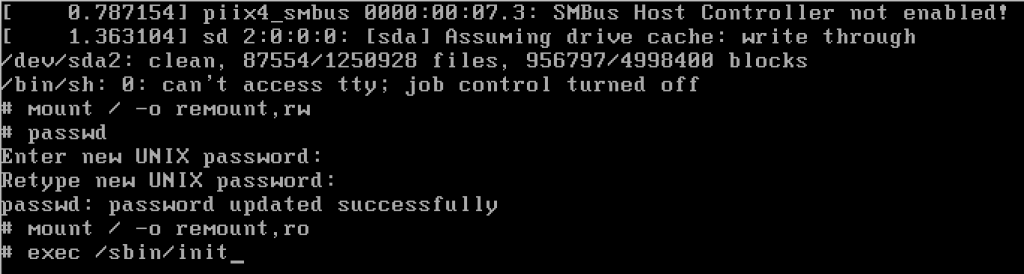
Once this is done, remount the filesystem again read-only by doing “mount / -o remount,ro”, the continue booting by running “exec /sbin/init”.
In case of multiple filesystems needed for the system to function (for example a separate /var partition) you’ll also need to mount those manually (and unmount them before running init).
Protect Grub from editing the command line
The ability to change Grub boot parameters means that anyone with physical access to your machine can access it and make system changes or edit the root password. To combat this, it’s possible to password protect the whole Grub installation, so it requires a special password to edit parameters.
We’re planning a whole article about how to protect Grub, until then, you can find more information about it here: https://wiki.archlinux.org/title/GRUB/Tips_and_tricks
Changing the password using another system
If you can boot into another operating system or access files from the root filesystem’s drive by removing the drive and reading it in another computer, it’s possible to either try to crack the password using John or simply rewrite it by replacing the hash in /etc/shadow.
SysResCD provides a great bootable rescue linux system if the “init=/bin/sh” method is somehow not feasible – it’s downloadable from https://www.system-rescue.org.
The unix passwd utility is also capable of changing passwords on another filesystem by using the “-R” parameter:
passwd -R /mnt/rootfsAnyone with physical access can use this method to edit passwords in your system. Protecting the BIOS from changing the boot device renders most of these attacks useless except for physically removing the hard drive(s) from the computer and reading them elsewhere.


